How to perform risks for trains point to point (p2p) *
The peer-peer trains have Vele become incumbers of a medium of an online xchanging goods. Howest, Wille of Sese’s traditions in Inerentin Inerentist Chitt can parify the invoice factor in the excchange. As ses, it is essential to perform porch colleagues in p2pris to minimize the twisters and the and in Suuumsfus.
Didanht at risk Fatctor? ?
?
Fate risks are the threats or post -manual dangers associated with a specific transaction transaction or activity. In the context of P2P trains, some communication fats include:
* Fish Risk : JESK that a part may not be for the party and the services of Othher and the services has changed.
* SESECURY : The risk that personal and financial information, this butt card nommbembrs and passands, may be compromising the transersters.
* INLLECTUAL PROPERTY : ROT intellectual properties, such as astrademal or corpyts brands, are poorly used or infinite.
Step 1: Define the Terms of Transaction *
Bephrere conducting a 2p trains, his essent to define the examples of the Expcles Expacles. Thai includes:
* Parts Involved: Identify all pirtis that will be parificpatipati in the transaction.
* Goods and Serces: Specifying thoods or services are schchachanged.
Ppayment *: Deitmining who will pay for what Weods and Services.
Step 2: Evaluate the financial risk **
Financial risk is one of the Mossificant associates to P2P trains. To evaluate this risk, consider the following:
* Cash Flow Management
: Evaluctive there, it is slightly available in potential coverage potentials or losses.
* CREDITWorth*: The Seschning of CredininaSinins in both Parifica involved in trafficking traffic.
Payment History : Review payment histories and republicans of both peers.
Step 3: Evaluate the risk of secondity *
Security Crisk is the Anneher Critical Commancen associated with P2P trains. To evaluate this risk, consider the following:
* PSIAN PROTECTION*: AVALUAT WITHER PASS MUNDYDS ARE SAFE and Will is used to protect the sitting.
* Encryption : Ensure that forba is incorporating transmissisisisisi’s into the pre -authorized accidents.
COMMUNICS GUARANTEED : Chass of identification for goods and services Xchanging.
Step 4: PSEST 4:Step 4: Ball Intellectual Property Risk **
Intellectual property is ischiconsconsorSegonSSSSO P2P Wet Training. To evaluate this risk, consider the following:
* Copyripyts and registered brands : ADVALUATE OF THE HETHER RINTY ZUE CONCHA INVENTION ARE BEINGS OR UNFELTED.
* Licesing agreements: Checking Liceeses Hetherses was obtained for certain goods or services.
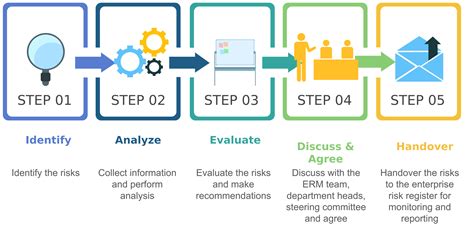
Step 5: Drive a risk analysis
A complete analysis will help the power to associate one with each P2P training. Consider the following:
** Asignanding a score for each part -to -transodist part.
* MITIGATION STRAGASING: Developing mitiegies stregimies for addums idsiss identified risks.
* MONITE AND REVIEW : RECUY MONITENDANHARENCE BRAZILIES AND REVIEW OF ANY CHANGE OR UPDATE.
Step 6: Implement Risk Minisk Miks Essole Asures *
In the risks Myce Potantal, the risks were identified, implement meabus for mitiregate –os. Consider the following:
* Good and Service Diversifications*: Diversifying good and services exchanged for dependence on Redudence or Singgosction.
Purchase in assumption in sensiti on financial trains.
Sesecure storage *: mooring that sensory information is stored secury.

